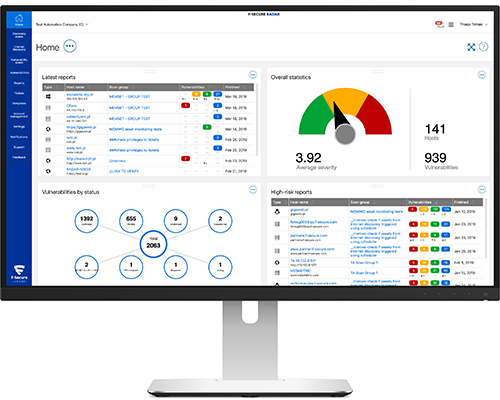
simple-surface-supercharged-hood
text.details.fr.fsecure-radar
- list.details.fr.fsecure-radar-1
- list.details.fr.fsecure-radar-2
- list.details.fr.fsecure-radar-3
- list.details.fr.fsecure-radar-4
- list.details.fr.fsecure-radar-5
- list.details.fr.fsecure-radar-6
map-your-attack-surface
text.details.fr.discovery-scan
- list.details.fr.discovery-scan-1
- list.details.fr.discovery-scan-2
- list.details.fr.discovery-scan-3
- list.details.fr.discovery-scan-4
identify-known-vulnerabilities
text.details.fr.system-scan
- list.details.fr.system-scan-1
- list.details.fr.system-scan-2
- list.details.fr.system-scan-3
- list.details.fr.system-scan-4
- list.details.fr.system-scan-5
test-application-vulnerabilities
- list.details.fr.web-scan-1
- list.details.fr.web-scan-2
- list.details.fr.web-scan-3
- list.details.fr.web-scan-4
- list.details.fr.web-scan-5
- list.details.fr.web-scan-6
discover-external-misconfigured
- text.details.fr.internet-asset-1
- text.details.fr.internet-asset-2
- text.details.fr.internet-asset-3
- text.details.fr.internet-asset-4
ensure-compliance-regulations
- text.details.fr.pci-compliance-1
- text.details.fr.pci-compliance-2
- text.details.fr.pci-compliance-3
- text.details.fr.pci-compliance-4
- text.details.fr.pci-compliance-5
- text.details.fr.pci-compliance-6